CAMS Research Framework
Successful cybersecurity leadership covers four critical areas shown in the pillars of our research program framework.
Explore the research projects associated with each area by clicking on that pillar.
Click here to see full diagram with list of projects
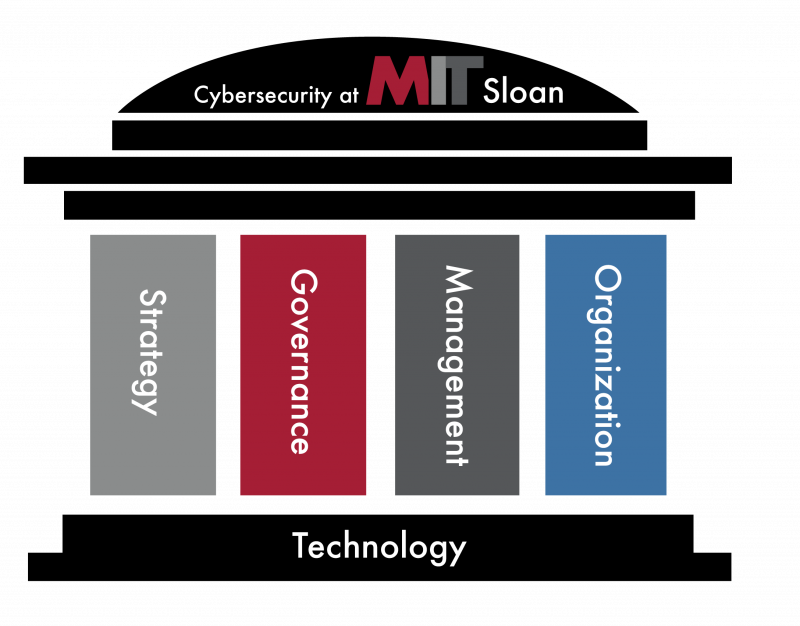
Strategy
- Board’s role in cybersecurity leadership
- Education of Boards and C-levels on cybersecurity
- Structure of cybersecurity workforce
- Prioritizing innovation and cybersecurity together
- Cybersecurity Information and mitigation sharing for competitive advantage
- International trade cybersecurity considerations
Governance
- House of Security: assessing cyber maturity
- Building organizational cybersecurity culture
- Bridging the IT/OT culture gap
- Framework for cyber education
- Ethics of cybersecurity
Management
- Cyber safety: research in accident prevention
- Cybersecurity of Industrial Control Systems (ICS)
- Cloud computing cybersecurity
- Cybersecurity of IoT and autonomous vehicles
- Vulnerability research
- Bridging the IT/OT culture gap
- Smart cities cybersecurity
Organization
- Building organizational cybersecurity culture
- Cyber insurance and risk mitigation
- Comparing national cybersecurity frameworks
- International cyber information sharing processes
- Creating security without sacrificing usability
- Success factors for cybersecurity companies
CAMS Research Framework
Successful cybersecurity leadership covers four critical areas shown in the pillars of our research program framework.
Explore the research projects associated with each area by clicking on that pillar.
Click here to see full diagram with list of projects
CAMS Research Framework
Successful cybersecurity leadership covers four critical areas shown in the pillars of our research program framework.
Explore the research projects associated with each area by clicking on that pillar.
Click here to see full diagram with list of projects
Click here to see full diagram with list of projects
Research Overviews
- (IC)3 Research Framework Overview
- Understanding the Cyber Attack Business
- Cybersecurity Culture Maturity Model
- Managing Risk with Cybersecurity Insurance
- House of Security: Assessing Cybersecurity Readiness
- Cybersecurity Concerns in the Adoption of IoT Technology
- Security Threats to Cyber Physical Systems (CPS)
- Cybersecurity and International Trade
- The Business of the Dark Web
- Building a Culture of Cybersecurity
- Cybersecurity Management in Pharmaceutical and Biotechnology Industries
- Cybersecurity Management in Pharmaceutical and Biotechnology Industries — one page
- Cybersecurity of IoT using Blockchain: Endpoint Security
- Understanding the Risks in the Mobility-as-a-Service Industry
- Balanced Scorecard for Cybersecurity Management
- Zero Trust Networks
Posters & Presentations
- A Smart IoT Integrity – First Communication Protocol via an Ethereum Blockchain Light Client presented to the 1st International Workshop on Software Engineering Research & Practices for the Internet of Things (SERP4IoT 2019) by Elizabeth Reilly, Matthew Maloney, Michael Siegel, and Gregory Falco, March 27, 2019.
- Status Update: Research Exploring Malware in Energy Delivery Systems (REMEDYS) presented to CREDC by Michael Sapienza and Keri Pearlson, February 15, 2019.
- GDPR Update – presented to Cybersecurity at MIT Sloan Research Team by Emerald de Leeuw, November 16, 2018.
- Cutting Edge Cybersecurity Leadership Research at MIT’s Sloan School – presented to the Society of Information Management (SIM) Boston Summit, October 23, 2018
- Creating a Cybersecurity Culture: (ISC)2 Survey Responses – presented to The International Information System Security Certification Consortium (ISC)2 October 8, 2018 by Keri Pearlson.
- Blockchain for Defensive Social Engineering – presented to Society of Information Management (SIM) April 12, 2018 by Greg Falco
- Building a Cybersecurity Culture: A Measurement Model and a Maturity Model – presented to Society of Information Management (SIM) Cybersecurity Special Interest Group February 2018 by Keri Pearlson
- Studying the Tension Between Digital Innovation and Cybersecurity – as presented at the AMCIS conference, August 2017, by Natasha Nelson and Stuart Madnick.
- PreventOTPhysDamage: Anticipating and Preventing Catastrophic OT Physical Damage Through System Thinking Analysis – as presented at the CRED-C conference, March 2017, by Matt Angle, Stuart Madnick, James L. Kirtley, and Nabil Sayfayn.
- The Wolves of Vuln Street: The 1st System Dynamics Model of the 0day Market – as presented at the RSA Conference, April 21, 2015, Moscone Center, by Michael Siegel and Katie Moussouris of HackerOne.
- Cyber Safety: A Systems Thinking and Systems Theory Approach to Managing Cybersecurity Applied to TJX Case – as presented at the International Atomic Energy Agency, Vienna, June 2, 2015, by Qi Van Eikema Hommes, Hamid Salim, Stuart Madnick, and Michael Coden.
- Advancing Cybersecurity Using System Dynamics Simulation Modeling For System Resilience, Patching, and Software Development (download) – as presented September 3, 2014, by Michael Siegel and James Houghton.
- Advancing Cybersecurity Using System Dynamics Simulation Modeling For Analyzing & Disrupting Cybercrime Ecosystem & Vulnerability Markets – as presented September 3, 2014, by Michael Siegel and James Houghton.
- Cyber Safety: A Systems Thinking and Systems Theory Approach to Managing Cybersecurity Applied to TJX Case – as presented by Hamid Salim and Stuart Madnick on September 3, 2014, by Stuart Madnick and Hamid Salim.
- MIT House of Security and Measurement of Security Perceptions in Corporations and Organizations – as presented on September 3, 2014 by Stuart Madnick.
Early Research Papers
(Members have access to more recent papers on the Members Only page)
- “Health Care and Cybersecurity: Bibliometric Analysis of the Literature” by Mohammad S. Jalali, Sabina Razak, William Gordon, Eric Perakslis, and Stuart Madnick. February 15, 2019.
- “The Internet of (Wonderful and Scary) Things” by Mohammad Jalali. January 2019.
- “For What Technology Can’t Fix: Building a Model of Organizational Cybersecurity Culture” by Keman Huang and Keri Pearlson. January 2019.
- “Enhancing Cybersecurity Education through High Fidelity Live Exercises (HiFLiX)” by Johan Sigholm, Gregory Falco, and Arun Viswanathan. September 2018.
- “Measuring Stakeholders’ Perceptions of Cybersecurity for Renewable Energy Systems” by Stuart Madnick, Mohammad S. Jalali, Michael Siegel, Yang Lee, Diane Strong, Richard Wang, Wee Horng Ang, Vicki Deng, and Dinsha Mistree. In book: Lecture Notes in Artificial Intelligence 10097, 2017, 67–77.
- “Trust and Collaboration to Enhance Cybersecurity” by Keman Huang, Keri Pearlson, and Stuart Madnick. December 14, 2017.
- “Decision Making and Biases in Cybersecurity Capability Development: Evidence from a Simulation Game Experiment” by Mohammad S. Jalali, Michael Siegel, and Stuart Madnick. December 2017.
- “The Internet of Things (IoT) Promises New Benefits — and Risks: A Systematic Analysis of Adoption Dynamics of IoT Products” by Mohammad S. Jalali, Jessica Paige Kaiser, Michael Siegel, and Stuart Madnick. November 2017.
- “Cybercrime-as-a-Service: Identifying Control Points to Disrupt” by Keman Huang, Michael Siegel, and Stuart Madnick. November 2017.
- “Beyond Keywords: Tracking the evolution of conversational clusters in social media” by James P. Houghton, Michael Siegel, Stuart Madnick, Nobuaki Tounaka, Kazutaka Nakamura, Takaaki Sugiyama, Daisuke Nakagawa, and Buyanjargal Shirnen. October 2017.
- “Decision Making and Biases in Cybersecurity Capability Development: Evidence from a Simulation Game Experiment” by Mohammad S. Jalali, Michael Siegel, and Stuart Madnick. August 2017.
- “The Internet of Things (IoT) Promises New Benefits — And Risks: A Systematic Analysis of Adoption Dynamics of IoT Products” by Mohammad S. Jalali, Jessica Paige Kaiser, Michael Siegel, and Stuart Madnick. August 2017.
- “Identifying and Mitigating Cyber Attacks that could cause Physical Damage to Industrial Control Systems” by Matthew G. Angle, Stuart Madnick, and James L. Kirtley, Jr. August 2017.
- “Cybersecurity Information Sharing Incentives and Barriers” by Priscilla Koepke. June 2017.
- “Striking a balance between usability and cyber-security in IoT devices” by Saurabh Dutta. May 2017.
- “Cyber Warfare Conflict Analysis and Case Studies” by Mohan B. Gazula. May 2017.
- “Cybersafety Analysis of the Maroochy Shire Sewage Spill” by Nabil Sayfayn and Stuart Madnick. May 2017.
- “Preparing for the Cyberattack That Will Knock Out U.S. Power Grids” by Stuart Madnick. May 2017.
- “Institutions for Cyber Security: International Responses and Data Sharing Initiatives” by Nazli Choucri, Stuart Madnick, and Priscilla Koepke. April 2017.
- “Studying the Tension Between Digital Innovation and Cybersecurity” by Natasha Nelson and Stuart Madnick. April 2017.
- “Trade-offs between digital innovation and cyber-security” (31 pages) by Natasha Nelson and Stuart Madnick. March 2017.
- “Diversity or Concentration? Hackers’ Strategy for Working Across Multiple Bug Bounty Programs” by Keman Huang, Michael Siegel, Stuart Madnick, Xiaohong Li, and Zhiyong Feng. December 2016.
- “Ukraine Power Grid Cyberattack and US Susceptibility: Cybersecurity Implications of Smart Grid Advancements in the US” by Abir Shehod. December 2016.
- “Analysis of the Digital Direct-to-Customer channel in Insurance” by Nithila Jeyakumar. December 2016.
- “Institutions for Cyber Security: International Responses and Data Sharing Initiatives” by Nazli Choucri, Stuart Madnick, and Priscilla Koepke. August 2016.
- “Cyber Safety: A Systems Theory Approach to Managing Cyber Security Risks – Applied to TJX Cyber Attack” by Hamid Salim and Stuart Madnick. August 2016.
- “Measuring Stakeholders’ Perceptions of Cybersecurity for Renewable Energy Systems” by Stuart Madnick, Mohammad S. Jalali, Michael Siegel, Yang Lee, Diane Strong, Richard Wang, Wee Horng Ang, Vicki Deng, and Dinsha Mistree. August 2016.
- “A Systems Theoretic Approach to the Security Threats in Cyber Physical Systems: Applied to Stuxnet” by Arash Nourian and Stuart Madnick. September 2014.
- “Cyber Safety: A Systems Thinking and Systems Theory Approach to Managing Cyber Security Risks” (Condensed 37 page version) by Hamid Salim and Stuart Madnick. September 2014.
- “Cyber Safety: A Systems Thinking and Systems Theory Approach to Managing Cyber Security Risks” (Full 157 page version) by Hamid Salim. May 2014.
- “Institutional Foundations for Cyber Security: Current Responses and New Challenges” (JITD) by Nazli Choucri, Stuart Madnick, and Jeremy Ferwerda. October 2013.
- “Inter-Organizational Information Sharing of Customer Data in Retail” by John Tengberg. May 2013.
- “Issues in Strategic Management of Large-Scale Software Product Line Development” by Jean-Baptiste Henri Nivoit. May 2013.
- “Challenges in Implementing Enterprise Resource Planning (ERP) system in Large Organizations: Similarities and Differences Between Corporate and University Environment” by Goeun Seo. May 2013.
- “Using System Dynamics to Analyze the Effect of Funding Fluctuation on Software Development” (ASEM) by Travis Trammell, Stuart Madnick, and Allen Moulton. March 2013.
- “Agile Project Dynamics: A System Dynamics Investigation of Agile Software Development Methods” (SD Conference) by Firas Glaiel, Allen Moulton, and Stuart Madnick. March 2013.
- “Towards better understanding Cybersecurity: or are “Cyberspace” and “Cyber Space” the same?” (WISP) by Stuart Madnick, Nazli Choucri, Steven Camiña, and Wei Lee Woon. November 2012.
- “Strategic Philanthropy for Cyber Security: An extended cost-benefit analysis framework to study cybersecurity” by Yiseul Cho. June 2012.
- “Comparative Analysis of Cybersecurity Metrics to Develop New Hypotheses” (WISP) by Stuart Madnick, Nazli Choucri, Xitong Li, and Jeremy Ferwerda. November 2011.
- “Institutional Foundations for Cyber Security: Current Responses and New Challenges” (revised) by Jeremy Ferwerda, Nazli Choucri, and Stuart Madnick. September 2011.
- “Exploring Terms and Taxonomies Relating to the Cyber International Relations Research Field: or are “Cyberspace” and “Cyber Space” the same?” by Steven Camiña, Stuart Madnick, Nazli Choucri, and Wei Lee Woon. August 2011.
- “Experiences and Challenges with using CERT Data to Analyze International Cyber Security” (AIS/WISP) by Stuart Madnick, Xitong Li, and Nazli Choucri. September 2009.
- “Explorations in Cyber International Relations (ECIR) – Data Dashboard Report #1: CERT Data Sources and Prototype Dashboard System” Stuart Madnick, Nazli Choucri, Steven Camiña, Erik Fogg, Xitong Li, and Fan Wei. August 2009.
- “Institutional Foundations for Cyber Security: Current Responses and New Challenges” by Jeremy Ferwerda, Nazli Choucri, and Stuart Madnick. September 2010.
- “A Systems Approach to Risk Management” (ASEM) by Nathan A. Minami, Stuart Madnick, and Donna Rhodes. November 2008.
- “An Economic Analysis of Policies for the Protection and Reuse of Non-Copyrightable Database Contents” (JMIS) by Hongwei Zhu, Stuart Madnick, and Michael Siegel. February 2008.
- “Preventing Accidents and Building a Culture of Safety: Insights from a Simulation Model” by John Lyneis and Stuart Madnick. February 2008.
- “Enhancing Vehicle Safety Management in Training Deployments: An Application of System Dynamics” by Kelvin F. H. Lim. February 2008.
- “The House of Security: Stakeholder Perceptions of Security Assessment and Importance” (FSTC) by Wee Horng Ang, Vicki Deng, Yang Lee, Stuart Madnick, Dinsha Mistree, Michael Siegel, Diane Strong, and Richard Wang. July 2007.
- “Using System Dynamics to Model and Better Understand State Stability” (SD) by Nazli Choucri, Daniel Goldsmith, Stuart E. Madnick, Dinsha Mistree, J. Bradley Morrison, and Michael D. Siegel. July 2007.
- “House of Security: Locale, Roles and Resources for Ensuring Information Security” (AMCIS) by Wee Horng Ang, Yang W. Lee, Stuart E. Madnick, Dinsha Mistress, Michael Siegel, Diane M. Strong, Richard Y. Wang, and Chrisy Yao. August 2006.
- “Improving National and Homeland Security through Context Knowledge Representation & Reasoning Technologies” (Book chapter) by Nazli Choucri, Stuart E. Madnick, and Michael D. Siegel. April 2006.
- “Understanding & Modeling State Stability: Exploiting System Dynamics” (IEEE Aerospace) by Nazli Choucri, Christi Electris, Daniel Goldsmith, Dinsha Mistree, Stuart E. Madnick, J. Bradley Morrison, Michael D. Siegel, and Margaret Sweitzer-Hamilton. January 2006.
- “Understanding & Modeling State Stability: Exploiting System Dynamics” (PCAS Final Report with Appendices) by Nazli Choucri, Christi Electris, Daniel Goldsmith, Dinsha Mistree, Stuart E. Madnick, J. Bradley Morrison, Michael D. Siegel, and Margaret Sweitzer-Hamilton. December 2005.
- “Policy for the Protection and Reuse of Non-Copyrightable Database Contents” by Hongwei Zhu, Stuart Madnick, and Michael Siegel. November 2005.
- “To Standardize Enterprise Data or Not? An Economic Analysis of Flexibility versus Control” by Chander K. Velu, Stuart E. Madnick, and Marshall W. Van Alstyne. November 2005.
- “Context Mediation Demonstration of Counter-Terrorism Intelligence (CTI) Integration” by Stuart E. Madnick, Allen Moulton, and Michael D. Siegel. May 2005.
- “Research Initiative to Understand & Model State Stability: Exploiting System Dynamics” (SD) by Nazli Choucri, Stuart E. Madnick, and Michael D. Siegel. February 2005.
- “Linkage Between Pre- and Post- Conflict: Exploiting Information Integration & System Dynamics” (IEEE Aerospace) by Nazli Choucri, Stuart E. Madnick, Allen Moulton, Michael D. Siegel, and Hongwei Zhu. January 2005.
- “Improving National and Homeland Security through a proposed Laboratory for Information Globalization and Harmonization Technologies” (LIGHT) by Nazli Choucri, Stuart Madnick, Michael Siegel, and Richard Wang. February 2004.
- “Global e-Readiness – For What? Readiness for e-Banking” (Journal of IT Development) by V. Maugis, N. Choucri, S. Madnick, M. Siegel, S. Gillett, F. Haghseta, H. Zhu, and M. Best. April 2004.
- “Improving UccNet-Compliant B2B Supply-Chain Applications Using a Context Interchange Framework” (BAI2004) by Steven Yi-Cheng Tu, Stuart Madnick, and Luis Chin-Jung Wu. February 2004.
- “Information Integration for Counter Terrorism Activities: The Requirement for Context Mediation” (IEEE Aerospace) by Nazli Choucri, Stuart E. Madnick, Allen Moulton, Michael D. Siegel, and Hongwei Zhu. November 2003.
- “LIGHTS: Laboratory for Information Globalization and Harmonization Technologies and Studies” by Nazli Choucri, Stuart Madnick, Michael Siegel, and Richard Wang. February 2003.
- “Attribution Principles for Data Integration: Technology and Policy Perspectives – Part 2: Focus on Policy” by Thomas Lee. February 2002.
- “Attribution Principles for Data Integration: Technology and Policy Perspectives – Part 1: Focus on Technology” by Thomas Lee. February 2002.
- “Why Not One Big Database? Principles for Data Ownership” (DSS) by Marshall Van Alstyne, Erik Brynjolfsson, and Stuart Madnick.
Why Join Cybersecurity at MIT Sloan?
Benefit from usable research! Cybersecurity at MIT Sloan (CAMS), formerly (IC)3, is focusing MIT’s uniquely qualified interdisciplinary faculty and researchers on the fundamental principles of cyberspace, cybercrime, & cybersecurity applied to critical infrastructure. Cybersecurity at MIT Sloan is a confidential academic forum in which leaders and managers can benefit from the experiences of CSO/CISOs across multiple sectors.
Community

Cybersecurity at MIT Sloan
Contact Us
Professor Stuart Madnick, Director, smadnick@mit.edu
Dr. Michael Siegel, Director, msiegel@mit.edu
Dr. Keri Pearlson, Executive Director, kerip@mit.edu
© Copyright 2025
Cybersecurity at MIT Sloan (CAMS) Privacy Statement
MIT Captioning & Accessibility